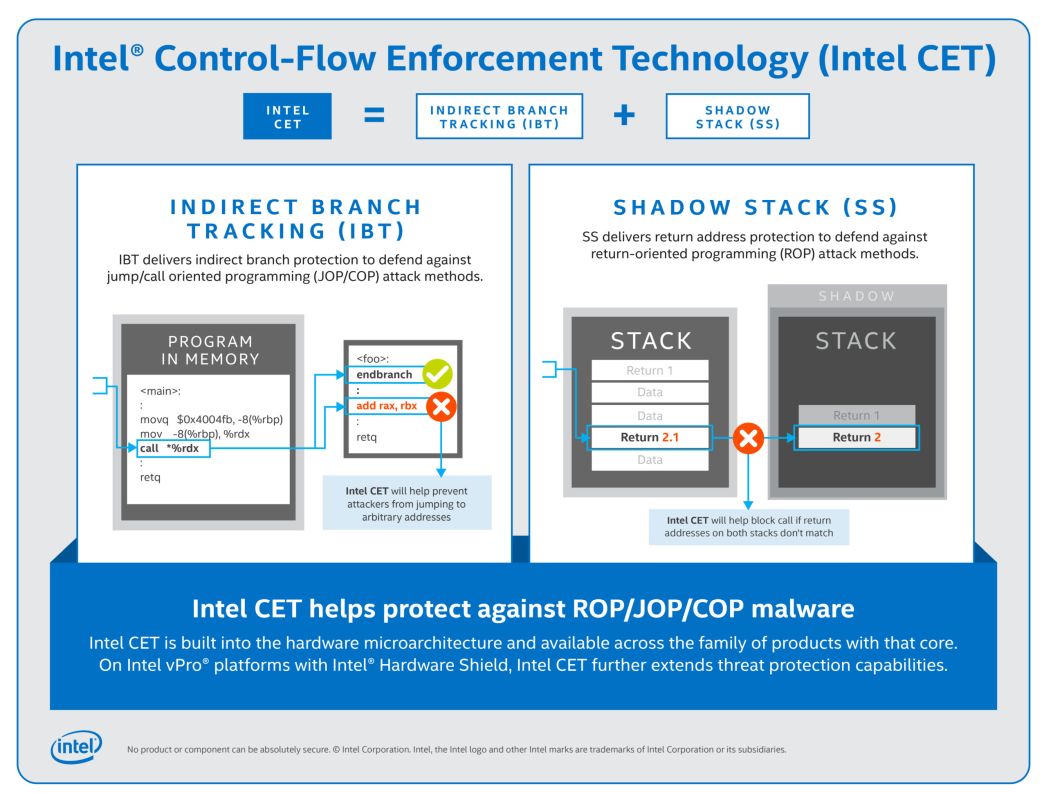
From Intel’s explanation, CET is designed to act as a bulwark of security capabilities that protects against common malware attacks on a CPU-level. Specifically, CET initiates the protection through two key capabilities: indirect tracking and shadow stack. To put it simply, indirect tracking is designed to deliver an indirect form of branch protection against jump and call-oriented programming (COP) attacks. While shadow stack is designed to protect against return-oriented programming (ROP) via the use of a method called return address protection. At the time of writing, Intel CET is expected to be first made available on the brand’s upcoming Tiger Lake mobile processor series. In conjunction with that, Intel has also announced that Microsoft will also be providing support for CET on Windows 10 via program called hardware-enforced Stack Protection. The program is obviously still in its testing phase, but for developers looking to get their hands on it, a preview of it is already available in within the latest Windows 10 Insider Preview. (Source: Intel)